Apache Ranger is a framework for enabling, monitoring, and managing the comprehensive data security across the Hadoop platform. Ranger simply helps a Hadoop admin with various security management tasks. It provides a mechanism to manage the security from a single pane for various components. With Ranger, you can control fine-grained access to various components of the Hadoop ecosystem.
Ranger has an Administration Portal you can use to define various policies for different components. Ranger plugins can be enabled for several HDP services. The following Ranger plugins are available:
- HDFS
- Hive
- HBase
- Kafka
- Knox
- YARN
- Storm
In this post, we will see how to create a ranger policy to define access to a particular database/table for a user. Before we create any policy, we first have to enable the Hive Plugin for Ranger using ambari.
Enable Ranger Hive plugin
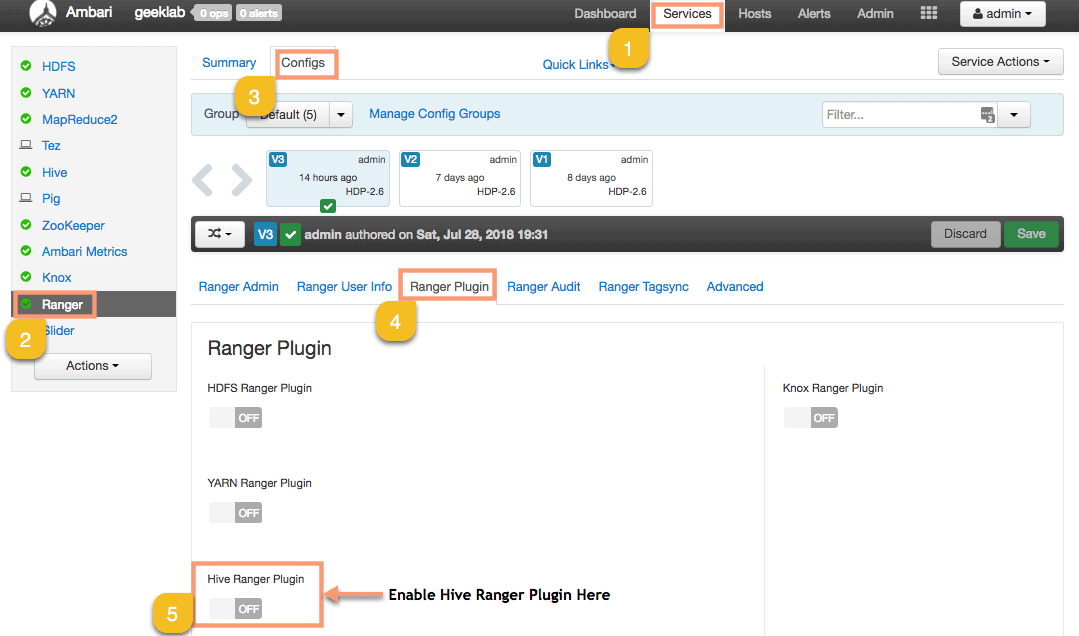
1. To enable Ranger Hive Plugin goto Services > Ranger > Configs > Ranger Plugin. Enable the Ranger Hive Plugin on this page.
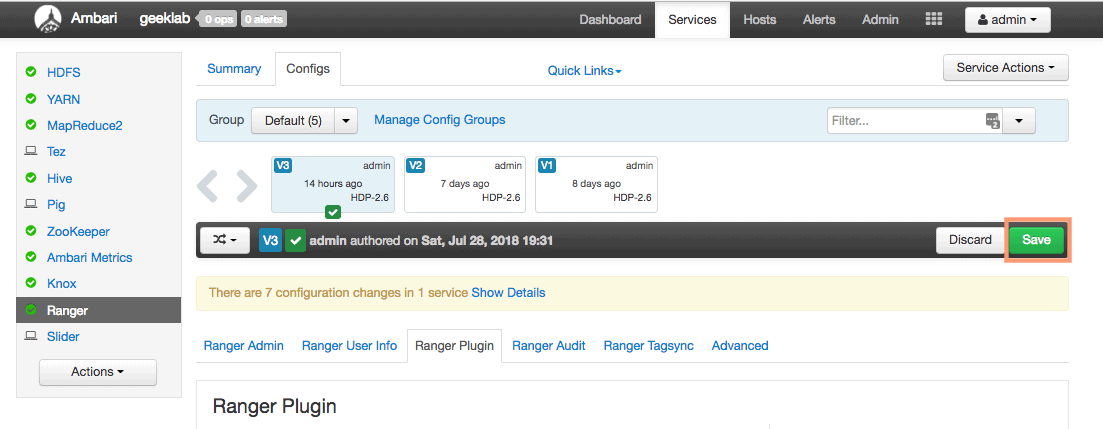
2. Save the config by providing an appropriate description note.
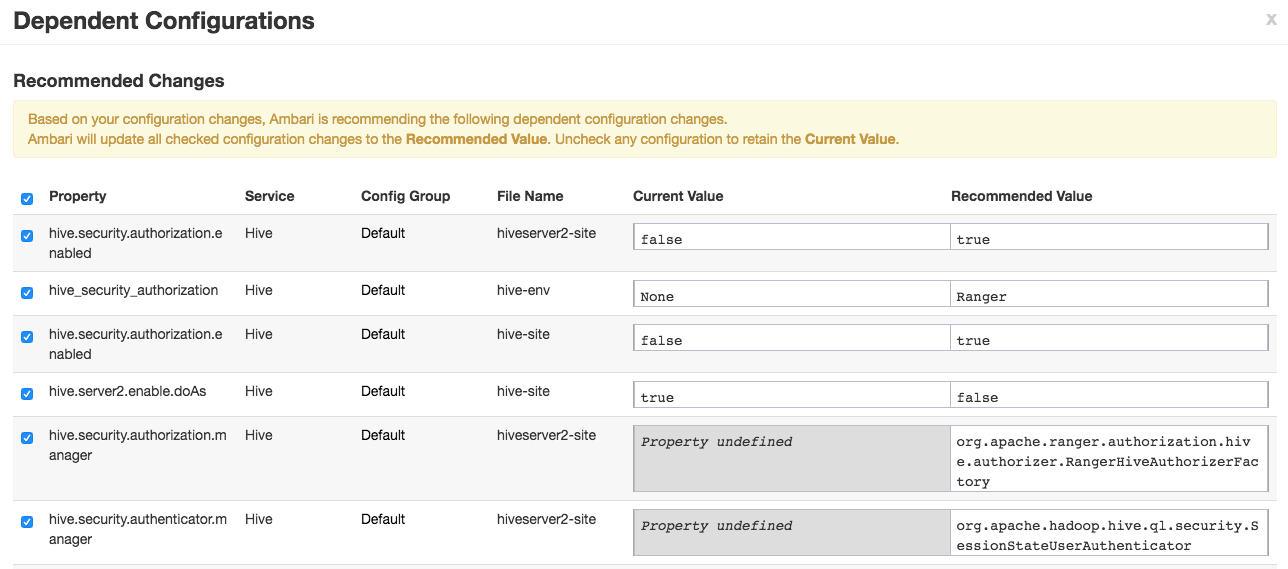
3. Ambari will prompt for some recommended changes to be done in order to enable the Ranger Hive Plugin. Accept the changes and proceed.
4. We need to restart the Hive Service for the changes to take effect.
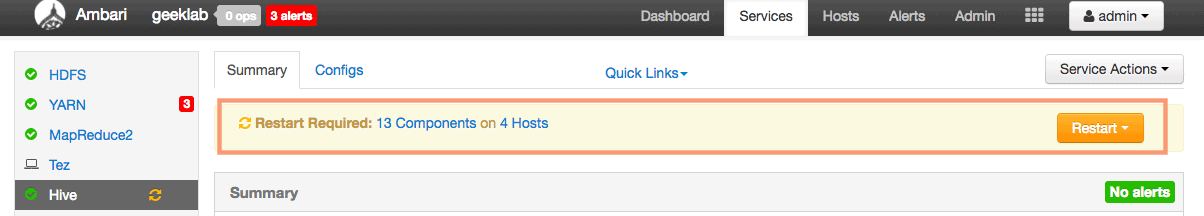
Overview of Ranger Admin UI and pre-configured policies for hive
You can log in to the Ranger Admin UI and check if the Ranger Hive Plugin is enabled and you can create policies. To login to the Ranger Dashboard use the default username/password of admin/admin.
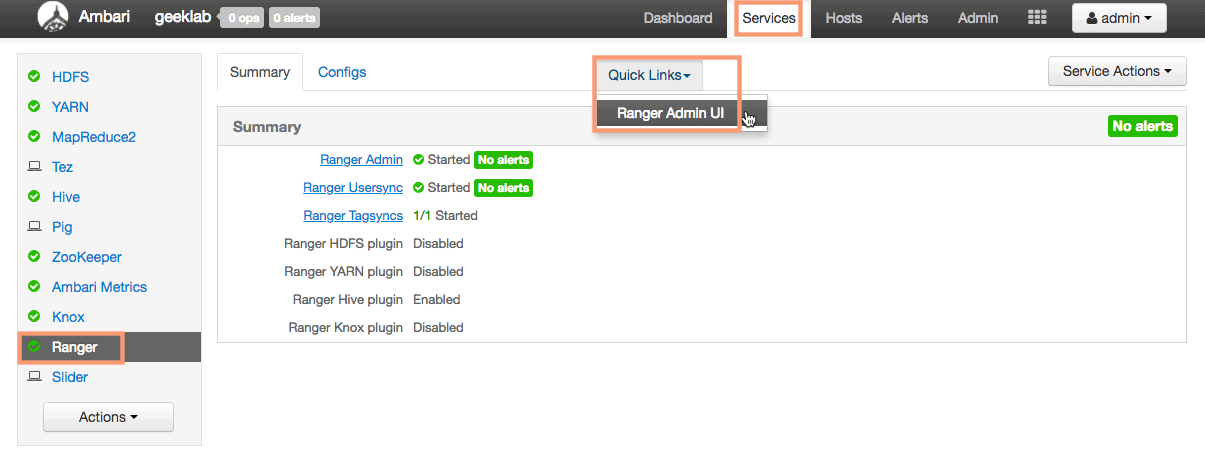
You can also goto the Ranger Admin UI with below URL:
http://rangerserver:6080
When you log in to the Ranger UI, the home page lists the various menus and types of policies that can be created using Ranger. As we can see the Ranger Hive Plugin is enabled and we can view the pre-configured policies for Hive.
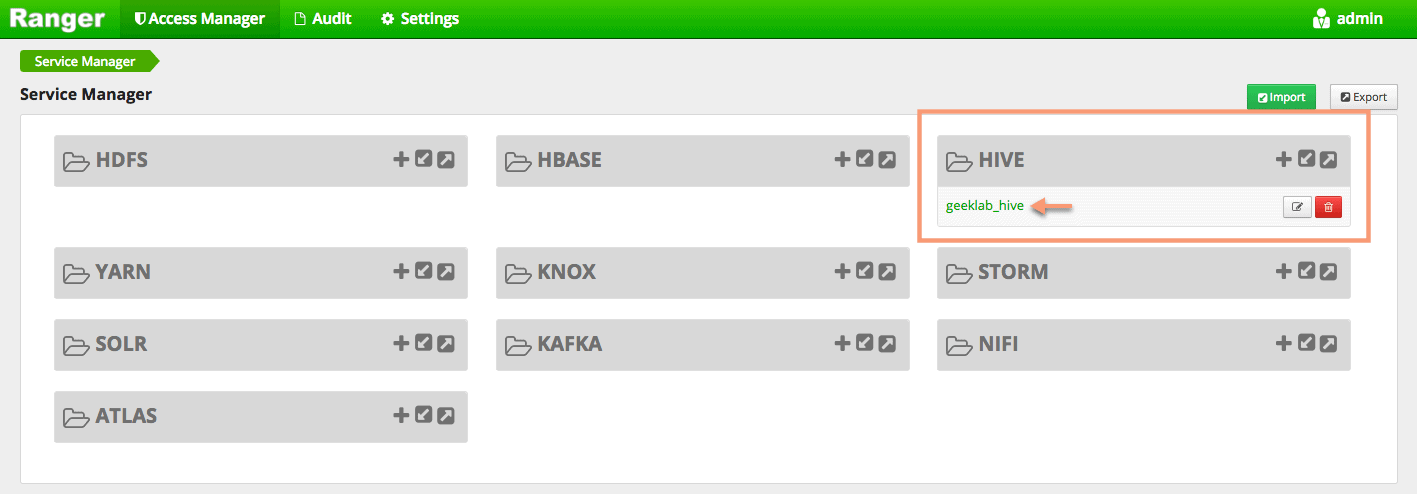
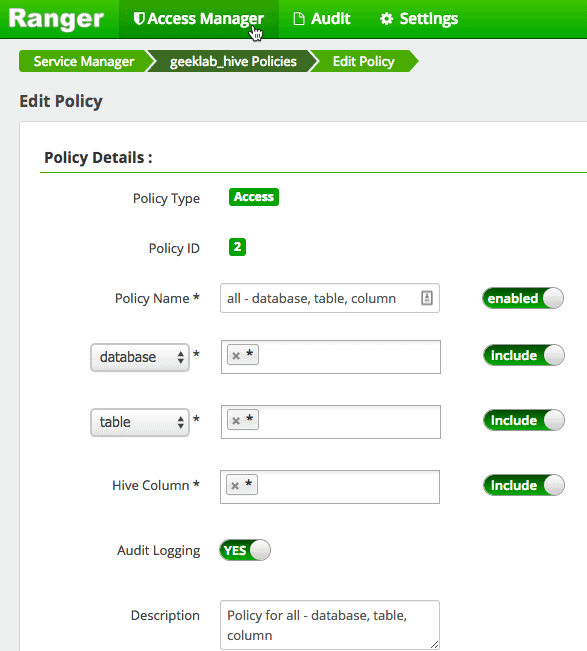
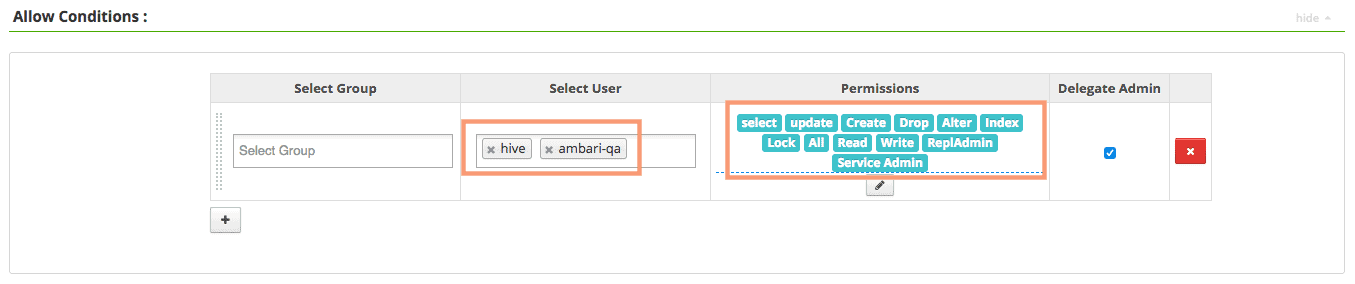
You can edit the pre-configured policies as shown below.
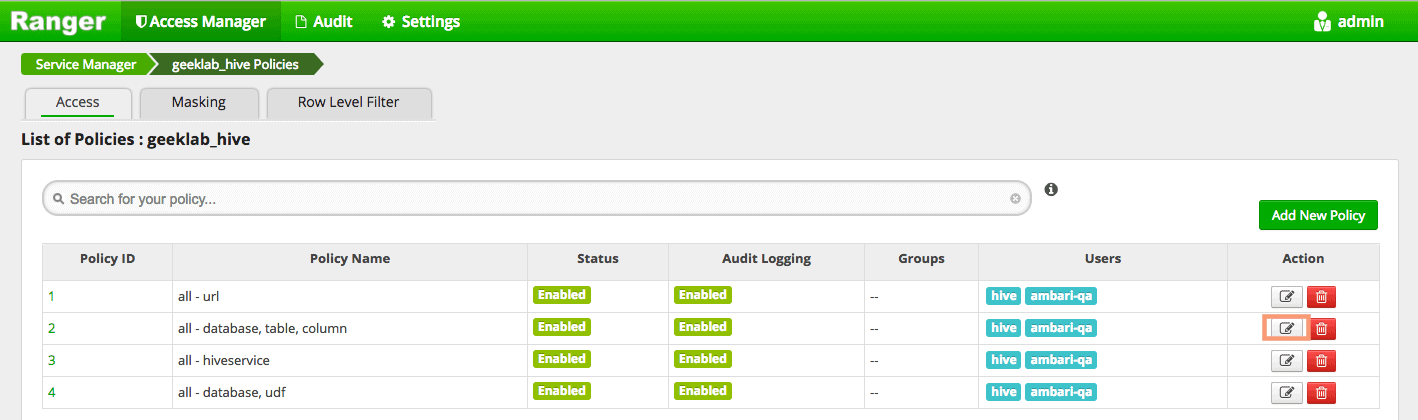
This particular policy provides ALL privilege access to the users “hive” and “ambari-qa”. You can add a new user/group and also modify the permissions on this page.
Creating a new Ranger hive Policy
Let’s create a new Ranger Hive Policy to allow access to a particular database (database name: default). The user will have only “select” privilege on all the tables in the default database.
1. Click on the policy group name under Hive.
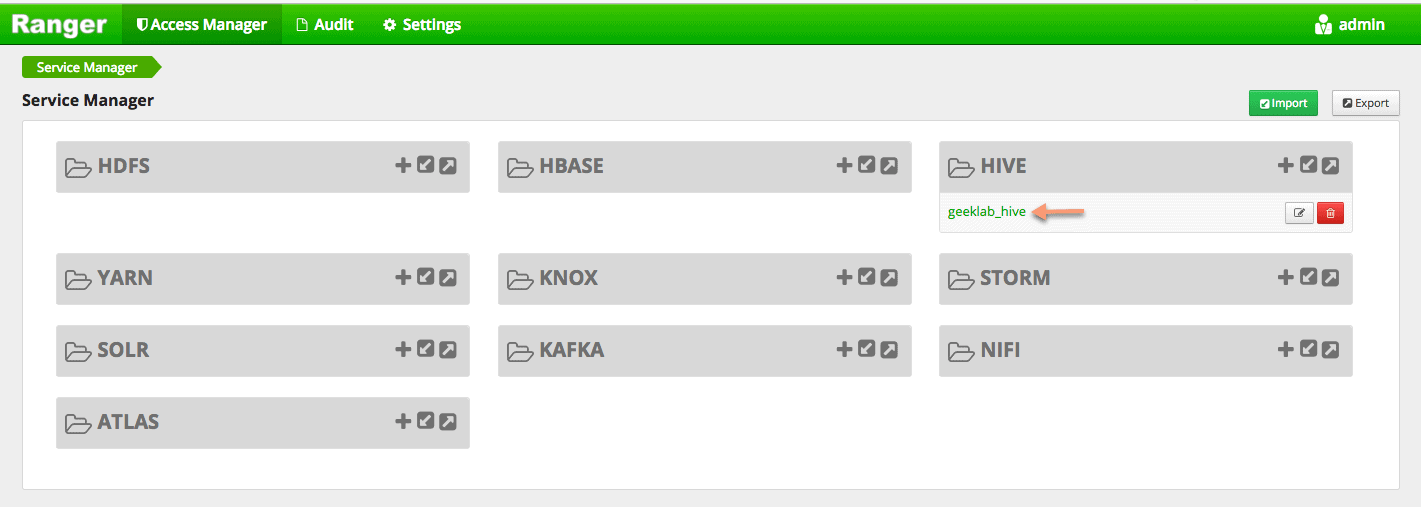
2. Now click on Add New Policy to open a new page, similar to the one shown below:
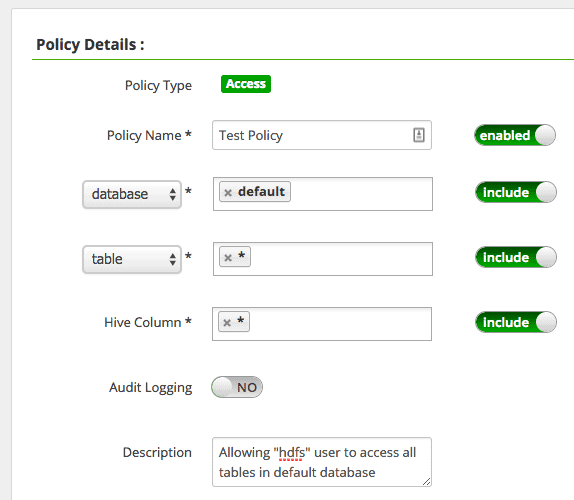
Provide the details like Policy Name, database name, table name etc.
3. In the “User and Group Permissions” section, we will assign the “select” permission to the user “hdfs”. Save the policy.
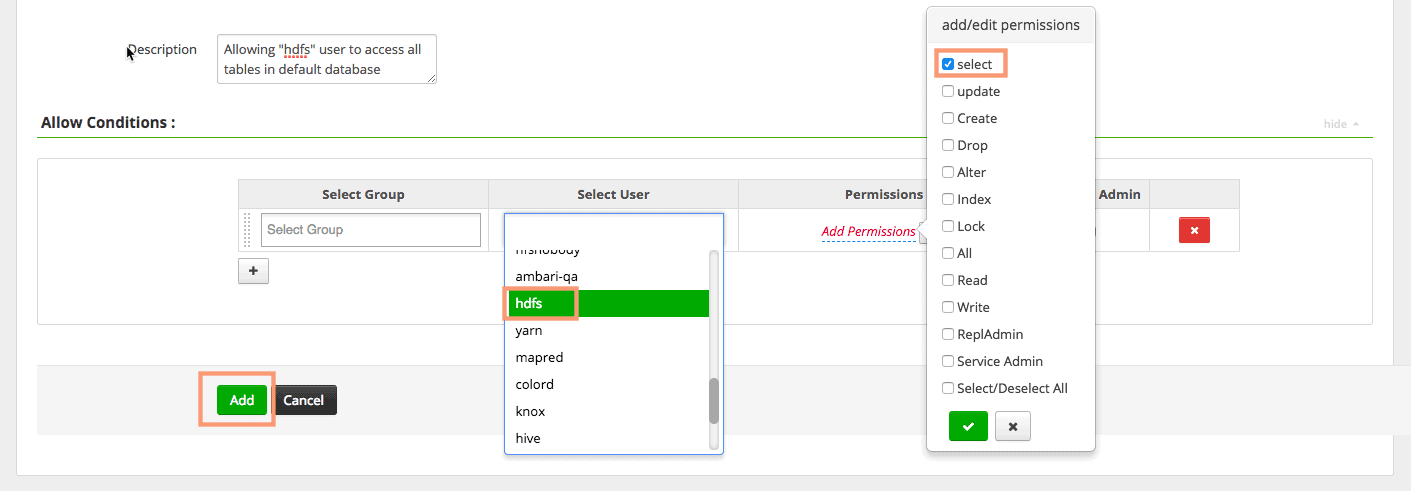
Verify the Ranger Hive Policy
Let’s connect to the Hive database using the user hive and test the policy we just created. I have already created a “test” table in the default database.
Getting the HiveServer2 JDBC URL from Ambari
We need to first get the HiveServer2 JDBC URL from ambari in order to connect the hive databases. Goto the Hive Service Page and copy the JDBC URL from the page.
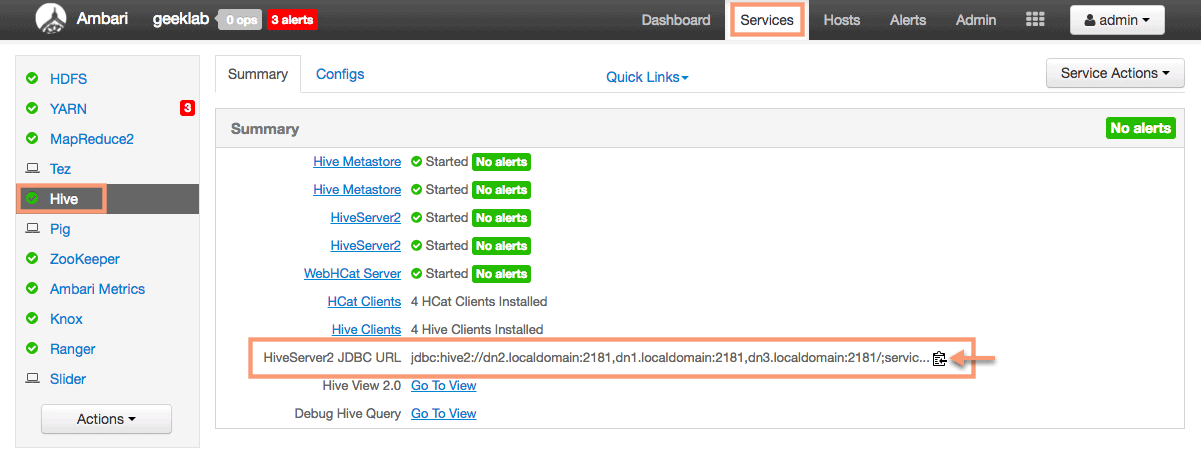
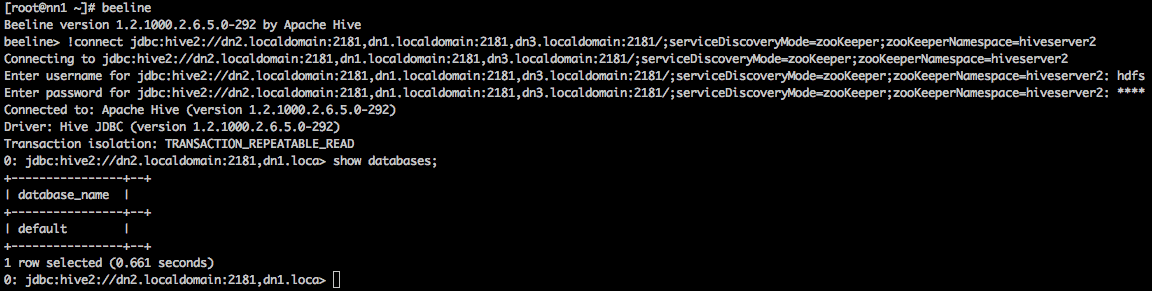
We can now connect to the hive default database using the user “hdfs”.
# beelineBeeline version 1.2.1000.2.6.5.0-292 by Apache Hivebeeline> !connect [HiveServer2 JDBC URL]
We can check if we can view the tables in the “default” database using the “hdfs” user. As shown below, we can query the table “test1” in the default database.
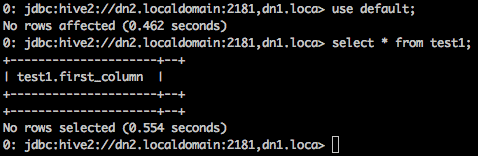
Let’s try to execute any other query on the table and see if the user has the privilege to drop the table “test1”.
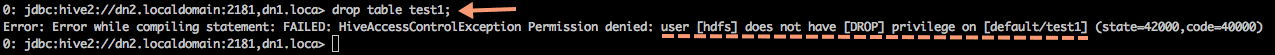
Granting user “hdfs” the “drop” privilege
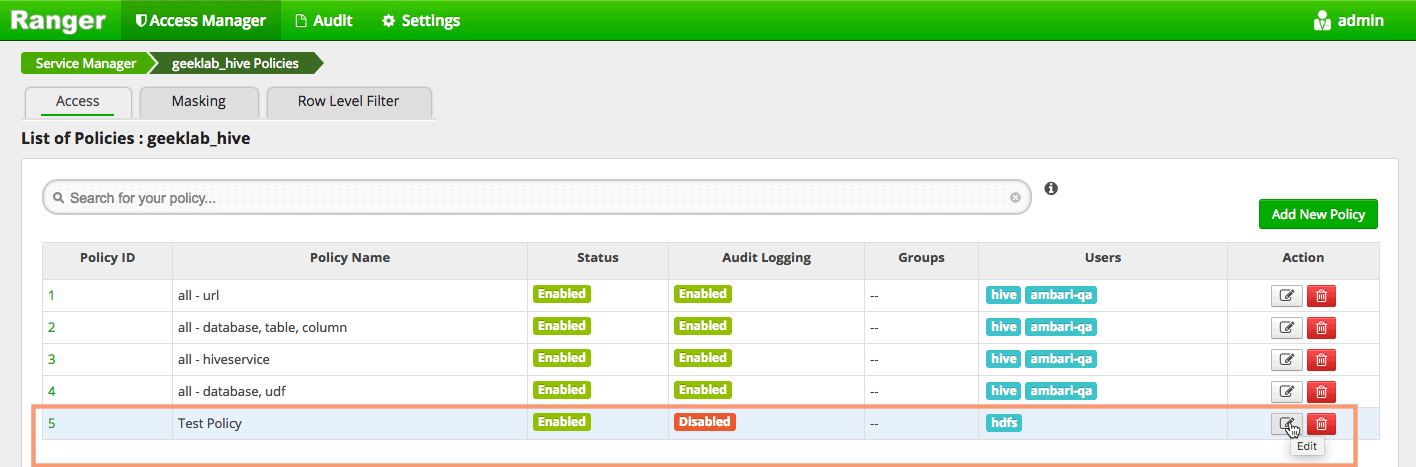
Let’s modify the policy and give the “drop” privilege to the “hdfs” user on all the tables of the “default” database. From the Ranger Dashboard, edit the policy we created earlier in this post.
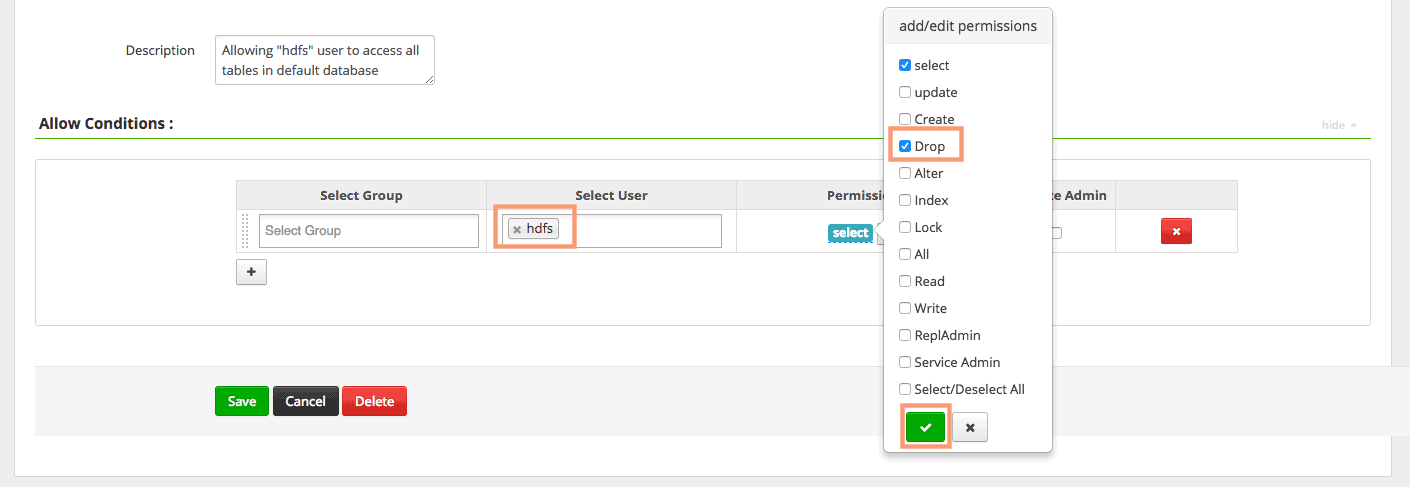
Assign the “drop” privilege to the “hdfs” user and save the policy.
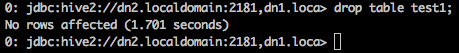
Wait for a minute or two for the policy to get updated across the cluster. Now try dropping the table again. This time the user hdfs is able to drop the test1 table.
No comments:
Post a Comment